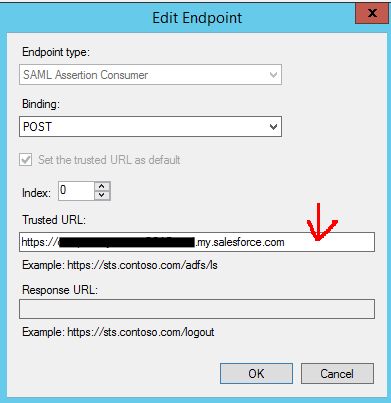
Here’s another weird issue in transitioning to the Lightning user interface in Salesforce.
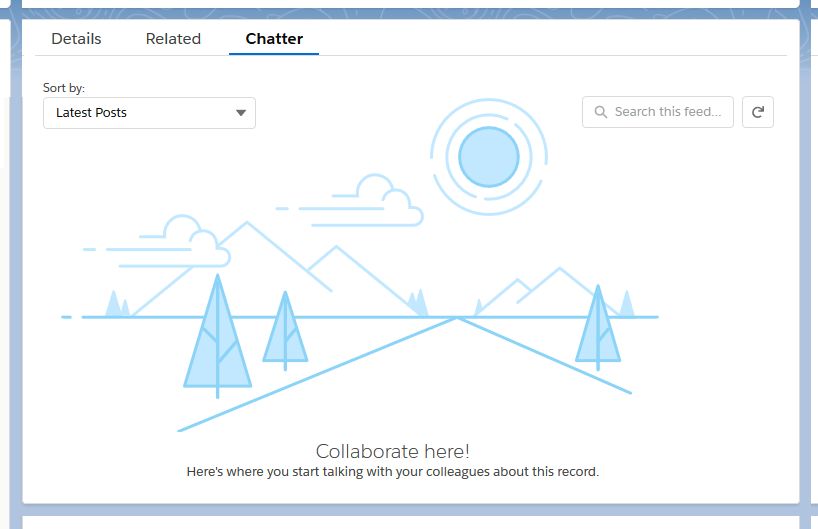
One of our users who regularly adds Chatter posts to records in the system, reported that they were unable to post a new Chatter thread against a record. On checking I likewise found that on the Chatter tab there was a bold invitation to “Collaborate here! Here’s where you start talking with your colleagues about this record.” But there was no way to actually post a message!
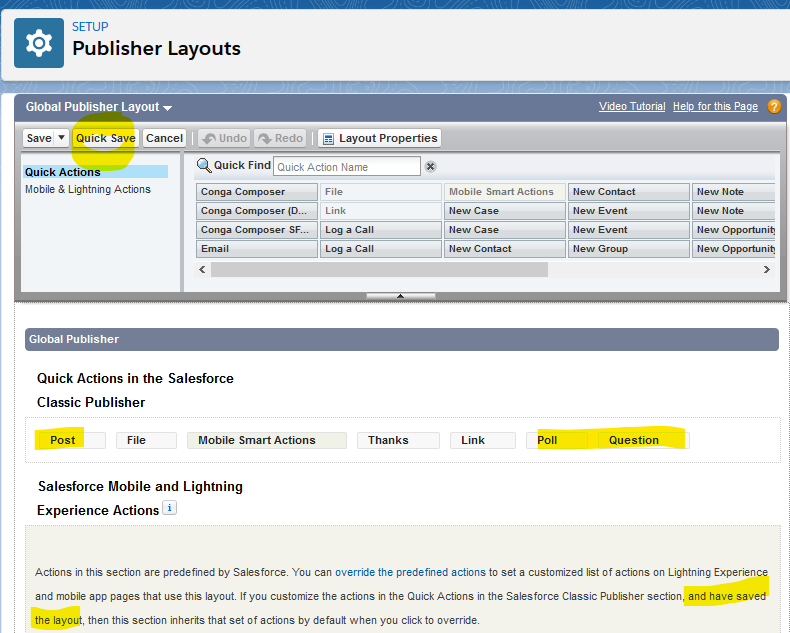
The issue turned out to lie with the Global Publisher Layout, which defines the actions that will be available for Chatter. From Setup search for “publisher”, click on “Publisher Layouts” and then edit the “Global Publisher Layout”
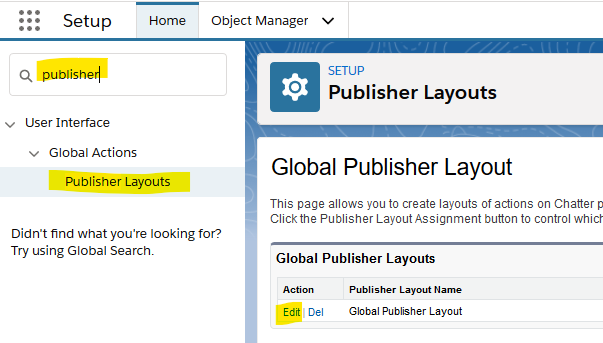 The “Classic Publisher” section defines what chatter actions will be available in the classic interface, and if no overrides are made in the “Lightning Experience Actions” section, then the Lightning interface should inherit the settings from the “Classic” section. However I found that it wasn’t until I saved the layout (without even making any changes) that the Chatter actions appeared in Lightning.
The “Classic Publisher” section defines what chatter actions will be available in the classic interface, and if no overrides are made in the “Lightning Experience Actions” section, then the Lightning interface should inherit the settings from the “Classic” section. However I found that it wasn’t until I saved the layout (without even making any changes) that the Chatter actions appeared in Lightning.
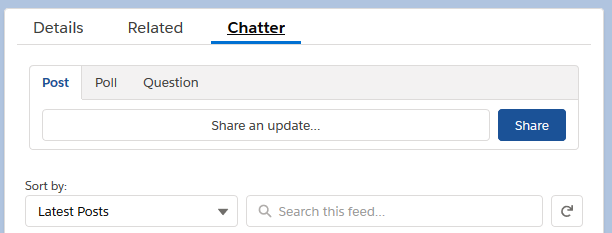
After clicking on “Quick Save”, the “Post”, “Poll” and “Question” actions appeared in the Chatter tab in the Lightning experience.